Introduction
Moving legacy applications into a software-defined network is rarely a straightforward process. Modern SDN platforms like Azure Local SDN offer flexibility, scalability, and automation, but legacy workloads often resist such transitions. The most common culprits are hard-coded IP addresses, non-compliant DNS logic, and fixed port assignments. These characteristics can disrupt seamless migration, introduce operational risk, and frustrate IT teams. This article explores step-by-step strategies, real-world workarounds, and automation patterns to address these classic obstacles.
Table of Contents
- Legacy App Challenges in SDN Environments
- Network Shaping Techniques for Hard-Coded IPs
- DNS Workarounds for Non-Compliant Applications
- Handling Static Ports and Protocol Dependencies
- Automating Workarounds with PowerShell, Bicep, and JSON
- Case Studies
- Comparison Table: Legacy vs SDN Approaches
- Checklists for Migration
- Troubleshooting Guide
- Conclusion
- AIOSEO Settings
- Yoast Settings
1. Legacy App Challenges in SDN Environments
Legacy applications often carry the following networking constraints:
- Hard-coded static IPs
- Manual DNS or HOSTS file entries
- Application-layer dependencies on specific ports
- Rigid firewall rules
- Lack of support for dynamic addressing or name resolution
Why do these matter in Azure Local SDN?
Azure Local SDN automates IP assignment, uses network overlays, and expects cloud-native behaviors. Legacy workloads can break if their expected environment is not replicated accurately.
2. Network Shaping Techniques for Hard-Coded IPs
Challenge
Applications reference fixed IP addresses, either in code, configuration, or third-party integrations.
Solutions
A. Preserving Original IPs in Azure Local SDN
Assign the same IP addresses to migrated workloads by explicitly configuring IP pools and static reservations.
PowerShell Example:
# Reserve a specific IP for a VM NIC
$ipPool = Get-SdnIpPool -Name "LegacySubnet"
$staticIP = "10.10.10.50"
Add-SdnIpReservation -IpPool $ipPool -IpAddress $staticIP -ResourceId "/subscriptions/xxxx/resourceGroups/LegacyRG/providers/Microsoft.Network/virtualNetworks/LegacyVNet"
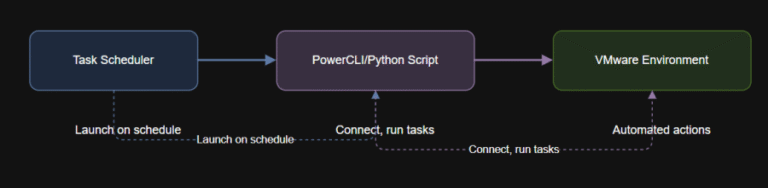
B. Network Address Translation (NAT) Overlays
Use Azure Local SDN Gateway Pools to translate original legacy IPs to new SDN-assigned IPs transparently.
Diagram:
 100vw, 846px”></figure>
<p><strong>PowerShell Example:</strong></p>
<pre class=)
# Create SNAT rule for incoming legacy IP
New-AzLocalGatewayNatRuleConfig -Name "LegacyIpSnat" -InternalIpAddress "10.1.2.5" -ExternalIpAddress "10.10.10.50"
C. Custom Routes
Configure static routes in the SDN to ensure packets for legacy IPs are forwarded correctly.
JSON Sample:
{
"name": "legacyStaticRoute",
"properties": {
"addressPrefix": "10.10.10.50/32",
"nextHopType": "VirtualAppliance",
"nextHopIpAddress": "10.1.2.5"
}
}
3. DNS Workarounds for Non-Compliant Applications
Challenge
Applications may ignore DNS or require static mappings, breaking when moved to dynamic or overlay networks.
Solutions
A. Host File Injection
Script the update of HOSTS files during migration or at VM deployment.
PowerShell Example:
$hostEntry = "10.1.2.5 legacy-app.local"
Add-Content -Path "C:WindowsSystem32driversetchosts" -Value $hostEntry
B. Private DNS Zones with Static Records
Use Azure Local SDN private DNS to create records matching legacy requirements.
Bicep Example:
resource legacyDns 'Microsoft.Network/privateDnsZones@2020-06-01' = {
name: 'legacy.local'
location: 'global'
}resource legacyRecord 'Microsoft.Network/privateDnsZones/A@2020-06-01' = {
parent: legacyDns
name: 'legacy-app'
properties: {
ARecords: [
{
ipv4Address: '10.1.2.5'
}
]
TTL: 3600
}
}
C. Custom DNS Forwarders
Deploy a DNS forwarder VM or container within the SDN to handle requests with legacy logic.
Diagram:
 100vw, 835px”></figure>
<hr class=)
4. Handling Static Ports and Protocol Dependencies
Challenge
Legacy software may only operate on fixed TCP or UDP ports, conflicting with security rules or port-mapping requirements.
Solutions
A. Static Port Rules in Network Security Groups (NSGs)
Define explicit NSG rules to allow only the required legacy ports.
PowerShell Example:
# Allow TCP 1433 for SQL legacy app
New-AzLocalNetworkSecurityRuleConfig -Name "AllowSQL1433" -Protocol "Tcp" -Direction "Inbound" -Priority 100 `
-SourceAddressPrefix "*" -SourcePortRange "*" -DestinationAddressPrefix "*" -DestinationPortRange "1433" -Access "Allow"
B. Port Forwarding via SDN Load Balancer
Map legacy ports to new SDN VM ports if needed.
Bicep Example:
resource legacyLb 'Microsoft.Network/loadBalancers@2022-05-01' = {
name: 'legacyAppLb'
properties: {
frontendIPConfigurations: [
{
name: 'loadBalancerFrontEnd'
properties: {
privateIPAddress: '10.10.10.100'
}
}
]
loadBalancingRules: [
{
name: 'legacyAppRule'
properties: {
frontendIPConfiguration: {
id: legacyLb.properties.frontendIPConfigurations[0].id
}
protocol: 'Tcp'
frontendPort: 12345
backendPort: 12345
enableFloatingIP: false
}
}
]
}
}
C. Application Gateway or Reverse Proxy
Route external traffic to the correct SDN resource and port using a Layer 7 proxy.
Diagram:
 100vw, 859px”></figure>
<hr class=)
5. Automating Workarounds with PowerShell, Bicep, and JSON
- Use ARM/Bicep templates to create SDN subnets, NSGs, and static IP pools matching legacy needs.
- Automate host file, DNS, and firewall rule injection via PowerShell DSC or VM extensions.
- Leverage SDN APIs for bulk changes.
PowerShell Example: Bulk HOSTS File Update Across VMs
$vmList = Get-AzVM -ResourceGroupName "LegacyRG"
foreach ($vm in $vmList) {
Invoke-AzVMRunCommand -ResourceGroupName $vm.ResourceGroupName -VMName $vm.Name -CommandId 'RunPowerShellScript' -ScriptPath 'Update-Hosts.ps1'
}
Published Links and References:
6. Case Studies
Case Study 1: Healthcare Application With Hard-Coded IPs
A hospital’s radiology system used hard-coded IPs in application configs and DICOM integrations. The migration team:
- Reserved those same IPs in Azure Local SDN’s static IP pools
- Used PowerShell scripts to automate reservation and network attachment
- Updated DNS and firewall rules to map to SDN-assigned resources
Related Published Links:
Case Study 2: Manufacturing Plant App With Legacy Port Dependencies
A process control application required UDP ports 502 and 20000. The Azure Local SDN team:
- Created explicit NSG and SLB rules for these ports
- Deployed a custom DNS forwarder for legacy hostname mapping
Related Published Links:
7. Comparison Table: Legacy vs SDN Approaches
| Challenge | Legacy On-Prem Solution | Azure Local SDN Solution |
|---|---|---|
| Hard-coded IPs | Manual static IP | IP reservation, NAT overlays |
| Static DNS | HOSTS file or static server | Private DNS zones, host file injection |
| Static ports | Manual firewall, open port | NSG, SLB, App Gateway rules |
| Rigid config | Siloed network, manual management | Automated policy, scripted enforcement |
| Change resistance | Manual edits, high outage risk | Automated scripts, minimal downtime |
8. Checklists for Migration
Pre-Migration:
- Inventory all hard-coded IPs and DNS dependencies
- Identify all static port requirements
- Validate application network diagrams
Migration:
- Script IP reservations in Azure Local SDN
- Implement custom DNS solutions as needed
- Create NSG/SLB rules for static ports
Post-Migration:
- Test connectivity and service resolution
- Monitor for failed lookups or blocked ports
- Update documentation
9. Troubleshooting Guide
| Symptom | Probable Cause | Resolution |
|---|---|---|
| Application fails to connect | Missing static IP mapping | Verify SDN IP reservation and NAT settings |
| Name resolution errors | DNS misconfiguration | Check private DNS zone, forwarder, or host file |
| Ports not listening/blocked | NSG or SLB misconfigured | Audit rules, confirm correct port/protocol |
| Legacy integration fails | Routing or NAT issues | Validate overlay/underlay mappings, static routes |
10. Conclusion
Modernizing legacy workloads with Azure Local SDN demands creative workarounds, automation, and careful planning. By leveraging SDN IP reservations, NAT overlays, custom DNS, and explicit port handling, network architects and sysadmins can shape robust, cloud-aligned networks even for the most stubborn legacy applications. These approaches reduce risk, streamline migrations, and set the foundation for future cloud-native evolution.
Disclaimer: The views expressed in this article are those of the author and do not represent the opinions of Microsoft, my employer or any affiliated organization. Always refer to the official Microsoft documentation before production deployment.